Basic Authentication: End of an Era
Back in September 2019, Microsoft announced it would start to turn off Basic Authentication for non-SMTP protocols in Exchange Online on tenants where the authentication protocol was detected as inactive. This is part of an overall movement to deprecate the less secure Basic Authentication, which is unfit to face the security challenges of the modern world, being subject to things like password spray attacks. It’s modern successor, modern authentication or OAuth2, uses a token and claim based mechanism contrary to sending accounts and passwords, and is the preferred authentication method. When combined with Azure AD for authentication, Modern Authentication also supports features such as Multi-Factor Authentication or Conditional Access.
The original date for disabling of Basic Authentication was October 13th, 2020. Then the world had other matters to deal with, and Microsoft extended the timelines. After initially postponing turning Basic Authentication off to the second half of 2021, the most recent – and final – start date for permanently turning the lights off for Basic Authentication is now set to October 1st, 2022, as per the article “Deprecation of Basic authentication in Exchange Online” and MC286990 in the Message Center. Mind the ‘start’ in start date, as flicking the switch for millions of tenants takes time before it becomes effective on your tenant. Organizations do need to anticipate on this change for the first of October 2022.

Until then, organizations can still (re-)enable Basic Authentication when they have a need, using the self-help system in the Microsoft 365 admin center. After entering “Diag: Enable Basic Auth in EXO” in the problem search query, the request will be checked, and Basic Authentication will get enabled. But with the end of support for Basic Authentication, so will this temporary workaround. On a side note, per end of 2020, newly created tenants already have basic authentication disabled by means of security defaults – if those organizations require Basic Authentication for some reason, they will also need to reconfigure security defaults which by default is an all or nothing option for all protocols.
So, with the doomsday counter ticking away for Basic Authentication, what are the consequences for Exchange related workloads organizations might wonder. In this article, I will try to address some of these concerns.
Interoperability with Exchange On-Premises
One might expect that most organizations running Exchange on-premises are running a supported version of Exchange server, especially after security-related issues such as Hafnium and ProxyShell in 2021. The truth might be far from that. Despite Exchange 2010 reaching end of life in October 2020, I still meet customers hosting their mailboxes on Exchange 2010 (and I’m sure there might even be organizations running on older versions of Exchange). One could ask serious questions when an organization runs a business-critical application on an older operating system, with both likely not having received significant security patches for over a few years now.
With Exchange Online no longer supporting Basic Authentication, this might have consequences for organizations running Exchange on-premises if their version does not support modern authentication, e.g., Exchange Server 2010. If they have Exchange Hybrid configured, things like cross-premises federation might break. Also, if at some point they do decide to go hybrid, their options will be affected as they will need to go through Exchange 2016 to have the best experience. Additionally, their mailboxes are on pre-Exchange 2016 CU3, and until their mailbox gets moved to Exchange 2016 CU3+ or Exchange Online, integration with an application such as Teams will be affected.
Autodiscover
I also hear from organizations that are concerned about Autodiscover and what the impact of disabling Basic Authentication might have. To start with the good news, Autodiscover is not a target protocol for disabling. Reading carefully through the message center post or the Basic Authentication self-help wizard, the following protocols are mentioned to be in-scope for permanently disabling Basic Authentication in Exchange Online:
- Outlook, i.e., Outlook for Windows or Mac
- Exchange Web Services (EWS)
- Remote PowerShell (RPS)
- POP
- IMAP
- Exchange ActiveSync (EAS)
SMTP AUTH will only get disabled if it is not actively used, but it can still be enabled after October 2022.
Tenant
Organizations that created their tenant before August 2017, had modern authentication turned off by default for Exchange Online. Unless the organization already enabled this, or when it was turned off for whatever reason, modern authentication needs to be enabled running Set-OrganizationConfig -OAuth2ClientProfileEnabled $true in Exchange Online Management shell. Alternatively, it can also be set via the Office 365 admin center via Settings > Org Settings > Modern Authentication > Turn on modern authentication for Outlook 2013 for Windows and later (recommended).
IMAP and POP
These older protocols are still used by a variety of e-mail clients, but also applications that interact with mailboxes. These applications will need to support Modern Authentication if they want to keep functioning. Fortunately, most popular e-mail client applications will, such as Thunderbird. I wrote an article on configuring your tenant for using Thunderbird with IMAP and OAuth2 earlier. Note, however, that this does not cover any other applications or custom software which uses IMAP; those need to be checked if they support OAuth2, and when needed might need work from vendor or the admin that created that script and hopefully has not left the organization.
Migration
The Exchange Online migration service uses a pull or push mechanism to pull data in from Exchange on-premises when onboarding or push data out to Exchange on-premises when offboarding. Since Exchange on-premises will still support Basic Authentication and NTLM for RPC/http, onboarding and offboarding should continue to work. That is, unless you are running Exchange 2019 CU2 or later to host your mailboxes, configured Hybrid Modern Authentication, and disabled legacy authentication protocols via an authentication policy. In that case you need to make a new policy with exceptions for the migration service accounts. Cross-premises federation with Exchange 2013 will use OAuth and is not hindered by a blocking legacy authentication policy.
If you are using a 3rd party solution to onboard mailboxes, from Exchange on-premises or from other environments, check if the product supports Modern Authentication or not for Exchange Online and the protocol used by the solution. For example, there are solutions that will use Exchange Web Services instead of RPC/http when extracting or ingesting mailbox data from or on Exchange Online.
PowerShell
Organizations that use scripts to perform tasks against Exchange Online need to verify them using the new Exchange Online Management PowerShell module. Despite this module being around since June 2020, not all organizations use it, and some are not even aware of it. It also often happens that a partner set up automated tasks running script using PowerShell remoting or the original click-to-run Exchange Online v2 (the original one that supported MFA), using Basic Authentication interactively or with a stored credential. Those organizations might have an unpleasant experience in October, unless they investigate their toolset and take action.
Unfortunately, there is no automated way to test or convert existing scripts with the EXOv2 module. Some cmdlets have different parameter sets or return subsets of properties, in which case an SME needs to have a proper look at it. But this might be a good topic for another day.
Exchange Web Services
The API which has been replaced by Microsoft Graph API as the API of choice for Exchange Online, has supported Modern Authentication for quite some time. However, scripts or applications that use EWS need to support this authentication as well, and unfortunately that is not always the case. It is up to the vendor of the application or owner of the script to add support for Modern Authentication to it. Just hope the creator of that IDM script that is running as a scheduled task somewhere can still be tracked down.
Note that in 2018, Microsoft already announced EWS would no longer be invested in for Exchange Online, and over time infrequently used API calls are being removed from Exchange Online. The first set of 25 API calls to be deprecated on March 31th, 2022, were announced on October 5th, 2021. So, while EWS will be supported until October 2022, there is a need for Exchange Online applications or tools to add or convert to Microsoft Graph API support. The consequence of this split is that eventually applications will contain specific code to interact with Exchange on-premises or Exchange Online, instead of being able to use a single API.
Clients
By now it should be no surprise that you need clients that support Modern Authentication. For Outlook for Desktop this could be Outlook 2013 or later (Outlook 2013 requires registry key), Outlook 2016 for Mac or later, Outlook for iOS or Outlook for Android, or Mail for iOS 11.3.1 or later. Of course, Microsoft 365 Apps for Enterprise, formerly known as Office 365 ProPlus, is also supported. I often find that organizations running old versions of Exchange also run equally old Office versions, so they potentially are looking at a large project to also get their environment current and ready.
3rd party clients such as recent versions of Thunderbird or eM Client also can be made to work, as mentioned in the paragraph on IMAP and POP.
Mobile
When you configured Mail on your iPhone in the past, there is a possibility that your profile is still using Basic Authentication for Exchange ActiveSync if your tenant still supports Basic Authentication. When you get a new phone, you can migrate your data and settings to your new phone. This will migrate everything, including configured mail profiles and authentication settings.
Luckily, per an article on integrating Apple devices with Microsoft Exchange (Apple support site), we learn that Apple is working on the option to automatically upgrade accounts configured for Exchange Online on iOS14/iPadOS14 and later for Modern Authentication (OAuth2). The expectation is a silent transition for those clients, without requiring user-interaction or any other form of support or adoption materials. That said, there is yet no ETA, and with October 1st approaching closer every day, the dependency on the quality of the conversion for a smooth experience increases as well.
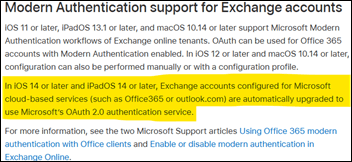
People using earlier versions of Apple Mail clients may need to manually remove and reconfigure the Exchange account, so it gets configured using Modern Authentication. The same applies to 3rd party clients on Android, such as Gmail on Android 9 and up.
People using Outlook for iOS or Outlook for Android will start using Modern Authentication.
Mail Relay
As said before, for applications or devices which need to send mail through the tenant using authenticated SMTP, SMTP AUTH does not get disabled. If it does get disabled due to non-usage, and there comes a point when you need to enable it again. Enabling SMTP AUTH is accomplished by running Set-TransportConfig -SmtpClientAuthenticationDisabled $False. Note that this enabled Basic Authentication as well as Modern Authentication for SMTP AUTH.
Monitoring
To monitor Basic Authentication usage, the monthly reports in the Message Center might be a good starting point. More details can be seen when viewing the Office 365 Basic Authentication Report, which can be accessed via the Azure portal, Sign-Ins Logs. Select Add filters, pick the Client App, then click the Client App: None Selected to get a choice of Legacy Authentication Clients to filter on.
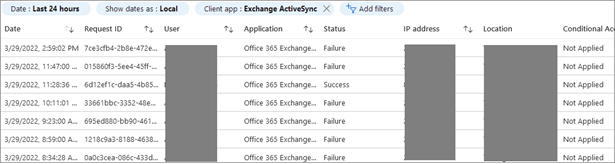
In this view, double-click an entry to open the details view, where you can see basic information such as account, device, application, authentication details, IP address and location. This should help to find people and devices still using Basic Authentication, after which they can be nudged to move in the right direction.
Final Notes
From personal experience, many of the organizations are not even aware of this upcoming change, or what authentication protocols are being used in their organization. Despite announcements in Message Center, including notifications such as MC345504 (disabling “Basic Authentication – Exchange ActiveSync”) for upcoming changes, monthly Basic Authentication usage reports, as well as informing organizations when Basic Authentication for a specific protocol gets disabled in their tenant, in my experience organizations see postponing of changes often as a trigger to relax urgency and delay actions. That is, until the inevitable day comes the change will happen. I hope with articles like these add to reach, and organizations will follow up on the call to action and move away from Basic Authentication when they can, rather than when they must.
Exchange Hybrid and Office 365 Monitoring and Reporting
On-premises components, such as AD FS, PTA, and Exchange Hybrid are critical for Office 365 end user experience. In addition, something as trivial as expiring Exchange or AD FS certificates can certainly lead to unexpected outages. By proactively monitoring hybrid components, ENow gives you early warnings where hybrid components are reaching a critical state, or even for an upcoming expiring certificate. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Access your free 14-day trial of ENow’s Exchange Hybrid and Office 365 Monitoring and Reporting today!








