Microsoft Defender Vulnerability Management
The worth proposition for the services in the EM+S E5 suite does not appear like it has been convincing to prospects for a when now. Around the final yr or so, Microsoft has been putting a large amount of get the job done into the Defender services to make improvements to that value proposition, and to supply a far better specialized protection solution for Microsoft 365 clients.
In the very last yr or so Microsoft has rebranded and reorganized the Defender purposes into Defender for Cloud Apps, Defender for Workplace 365, Defender for Endpoint, and Defender for Id. Whilst people four products and services are a excellent commence, there are still gaps in the security they supply.
To that end, Microsoft has extra a new solution in community preview to the Defender Suite, Microsoft Defender Vulnerability Management (DVM). DVM is focused at increasing vulnerability management in the subsequent locations:
- Protection baselines evaluation
- Browser extensions assessment
- Digital certificates evaluation
- Community shares assessment
- Blocking vulnerable apps
- Vulnerability evaluation for unmanaged endpoints
In this website publish we’re going to glimpse at the community preview for this new services. How to get it activated in your tenant, what it does, and where by I see it fitting into your in general protection architecture for Microsoft 365.
Activating the community preview
Though general public previews for numerous new Microsoft 365 characteristics are automatically added to tenants, the community preview for DVW necessitates a shorter process to activate. You can indicator up listed here. That course of action only took me a few of minutes, then I had new licenses in my tenant that I could assign to an admin account to achieve entry to DVM features. The moment that is complete, you will have entry to the feature we’ll deal with down below.
Exactly where is DVM?
The GUI for the Microsoft 365 Defender stack of apps is typically (but not entirely) homed in the Microsoft Security Portal. When this can make it a little complicated to differentiate the features of the distinctive programs in the Defender stack, it also offers us a “one halt shop” for Microsoft 365 stability configurations. Perhaps a independent portal for just about every application would be a very good concept, but then all over again probably this way is greatest.
The moment you have DVM certified and you have logged into the Stability Portal, you will uncover all the new DVM functions obtainable below the Endpoints segment on the remaining-hand aspect of the screen:
There are currently 7 subsections below Vulnerability Management right here. As this software is continue to in community preview, that may well improve right before DVM hits GA.
Checking out the Dashboard and Suggestions
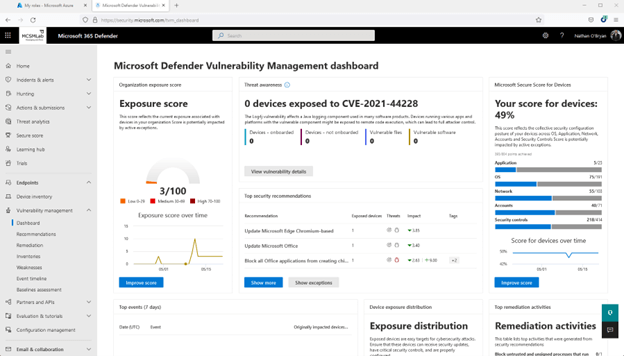
The very first space to take a look at is the dashboard. In this article you will come across a brief see of a handful of various measures of vulnerability within just your Microsoft 365 tenant.
In my tenant, you can see my exposure rating is low (3/100 is a good point. You want that quantity to be as reduced as feasible), and my safe score for gadgets isn’t terrific (49% implies I have remediated about half of the problems Microsoft screens to make up that rating).
Clicking on Enhance Rating on both of these widgets will choose you to the suggestions sub-portion, the place recommended remediations are thorough to aid you increase the stability posture of your tenant.
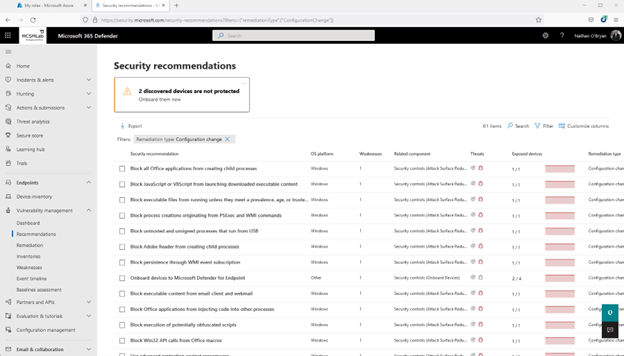
Down below is a screenshot of the recommendations page for my machine secure rating. With 61 things to address, it seems like I have to some work to do in my tenant.
Remediation
The remediation sub-area is for arranging the recommendations into lively tasks.
Heading back up to suggestions for my secure rating for units, I picked just one of the tips (in this circumstance “Update Office”), and then selected the Request remediation button at the base of the fly-out web page.
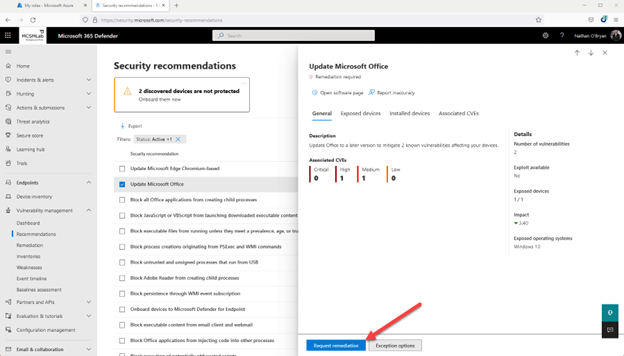
This will give you a brief wizard that lets you to mark that advice for remediation. It is by no usually means a complete-blown ticketing technique, but this seems like it could be handy for prioritizing the implementation of those people recommendations in your crew. Not super helpful for me, as I am the only administrator in my tenant.
Inventories
The inventories tab presents you an inventory of the apps, browser extensions, and certificates mounted on Home windows machines that have been inventoried into Endpoint Administration.
I do have an iPad that has Defender, but no applications from that system are inventoried below. This sub-segment will stock macOS, Linux, and Windows. iOS and Android devices are remaining out for now.
Weaknesses
The weaknesses sub-segment is nonetheless a different view of the identical details presented in a various way. Right here you will see vulnerabilities that can have an effect on your devices outlined by vulnerability title.
Underneath you can see I selected just one of the vulnerabilities that is similar to Place of work. It shows me that I have a person Windows 10 laptop computer that desires an Place of work update.
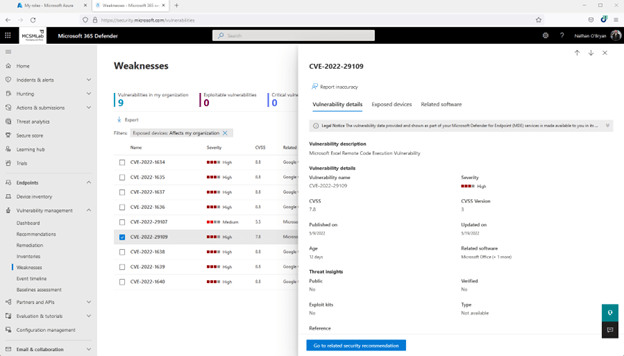
It’s telling me that updating Business on that 1 laptop will acquire treatment of the Suggestion, the Remediation that I opened from that Recommendation, and this Weak spot detailed right here.
When that level of redundancy probably is not necessary for a little tenant like mine, I do look forward to playing around with DVM in a a great deal bigger tenant. I believe this info would be considerably additional beneficial in a more substantial ecosystem where it’s additional challenging to maintain track of the diverse vulnerabilities affecting a deployment.
Occasion Timeline
Guess what is in the Function Timeline sub-segment. If you guessed yet another perspective of the same vulnerabilities, then you just earned a gold star for the day.
In the screenshot down below, you can see that I seriously will need to update Office on that notebook!
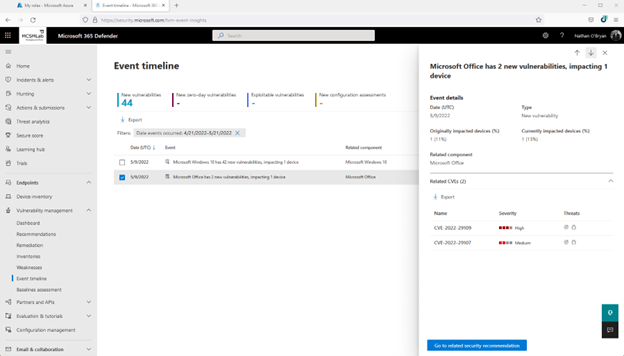
All over again, this is the same two Office environment vulnerabilities that are proven in a a bit distinctive watch. There is even a button here that will get you back again up to the Suggestions for these vulnerabilities.
Baseline Assessment
So much DVM has proven us a dashboard that summarizes the vulnerabilities stated in the following 5 sub-sections, then individuals very same vulnerabilities detailed in these 5 unique subsections. I don’t want to audio also “complainy” here, as this is very good vulnerability info that can definitely enable administrators greater protected their products, but I do think these sub-sections could be condensed into a solitary pane with some type of various views. I am not a UI designer, so possibly there is a very good reason Microsoft felt they essential all that authentic estate inside the Security Middle to present the identical information and facts various periods.
The Baseline Evaluation sub-area, nevertheless, does provide unique features. According to Microsoft Documentation:
“A protection baseline profile is a personalized profile that you can build to evaluate and observe endpoints in your corporation versus market protection benchmarks. When you create a security baseline profile, you are developing a template that is made up of various machine configuration configurations and a foundation benchmark to review from.”
To generate a Baseline Evaluation profile:
- From the Baseline Assessment sub-portion, pick out “+Create” in the upper left to make a new profile.
- Name your new profile and insert a description. Select Following.
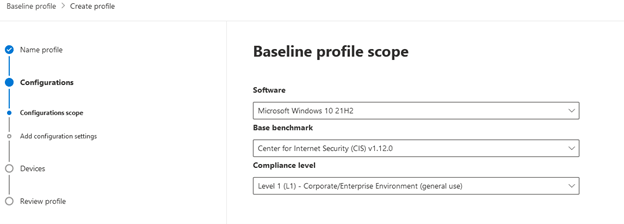
- Pick your profile scope by choosing software package to keep an eye on (Versions of Home windows 10 and 11 are stated in this article. Ideally Microsoft will insert extra application at a later on day), a baseline benchmark (I picked CIS v1.12.), and a compliance amount. Pick Future
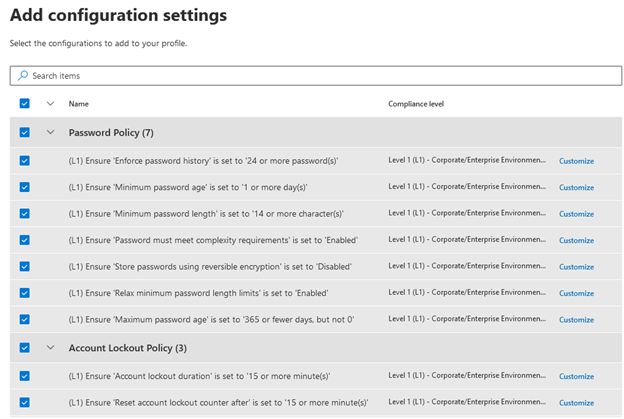
- Increase configuration configurations. Based on the benchmark and compliance stage selected on the previous webpage, you will see unique configuration settings you can decide on. With the picks I produced there are hundreds of distinct configuration options for me to choose from. I’m going to pick out them all for this take a look at profile, but you are going to want to commit some time on choosing solutions that meet up with your organization’s compliance wants. There is also a Personalize button to the suitable of just about every placing so you can edit just about every environment independently. At the time you’re accomplished, find Upcoming.
- Choose gadgets to assess. I only have a single product in my tenant to which this profile can apply, so I picked All product groups. Pick out Following, then assessment you profile options on the next web page and submit the profile. After you have submitted your bassline assessment profile, it will take some time for any new data to demonstrate up. The documentation claims 12 hours.
I’m going to permit that operate, then we’ll choose a deeper appear at the baseline evaluation and about DVM characteristics in a long term site publish.
With e mail remaining one particular of the most mission-critical equipment for businesses nowadays, how do you guarantee vital company interaction stays up and jogging? How do you display to senior management that more sources are wanted to fulfill developing need or that provider concentrations are remaining fulfilled?
Made by Exchange architects with immediate product or service input from Trade MVPs, ENow’s Mailscape will make your work less difficult by putting every little thing you will need into a one, concise OneLook dashboard, as a substitute of forcing you to use fragmented and complex instruments for checking and reporting. Easy to deploy and intuitive to use, get began with Mailscape in minutes somewhat than times.
Entry YOUR Cost-free 14-Day Demo and mix all key components for your Trade checking and reporting to hold your messaging infrastructure up and operating like a pro!
Products HIGHLIGHTS
- Consolidated dashboard check out of messaging environments health
- Quickly confirm exterior Mail circulation, OWA, ActiveSync, Outlook Anywhere
- Mail flow queue monitoring
- DAG configuration and failover checking
- Microsoft Security Patch verification
- 200+ built-in, customizable experiences, like: Mailbox size, Mail Traffic, Quota, Storage, Distribution Lists, General public Folders, Databases sizing, OWA, Outlook variation, permissions, SLA and cellular product reports









