Microsoft 365, formally Office environment 365, is maturing. It has been a lot more than 10 decades since the start of Business office 365, and the variety of migrations I see as a specialist are altering.
10 yrs back, I was doing migrations into Trade On the net one particular following a different. Workplace 365 started off as a place to place your e mail with it’s possible some constrained SharePoint and Skype for Enterprise products and services connected. As Business 365 matured into Microsoft 365 with significantly much more performance from SharePoint On-line, Groups, extra products and services like Endpoint Administration (Formerly Intune), a total host of protection and compliance resources, the form of initiatives I have been undertaking has progressed.
Now a honest total of the migrations I am executing entail tenant consolidations and splits. Corporations and other organizations that use Microsoft 365 are matter to all the regular financial forces that result in lawful entities to realign them selves. These organizational adjustments imply that extra and additional organizations require methods to collaborate in between separate Microsoft 365 tenants. Those organizational consolidations and splits usually have to have a bigger level of cross-tenant obtain among tenants possibly in advance of or just after the tenant migrations, but Microsoft 365 is just not developed to assist this sort of cross tenant collaboration.
Not too long ago, Microsoft has additional a new element to aid control that specific type of cross-tenant collaboration. In this site publish, I am heading to dive into the new cross-tenant entry settings that have not too long ago been additional to Azure Active Listing.
What are the new configurations?
Microsoft has extra the new cross-tenant accessibility options tab in Azure Energetic Directory beneath “External Identities”:
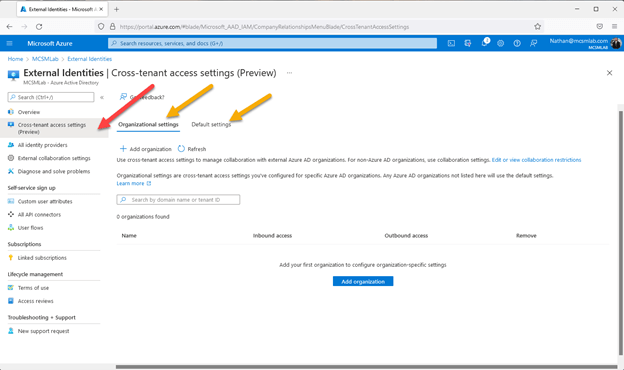
The red arrow in the picture higher than factors to the tab for the new cross-tenant entry configurations. The two environmentally friendly arrows position to the key pertinent sections of this new element.
We’ll start with the default configurations place. “Default options apply to all exterior Azure Advertisement corporations not stated on the organizational configurations tab. These default configurations can be modified but not deleted.”
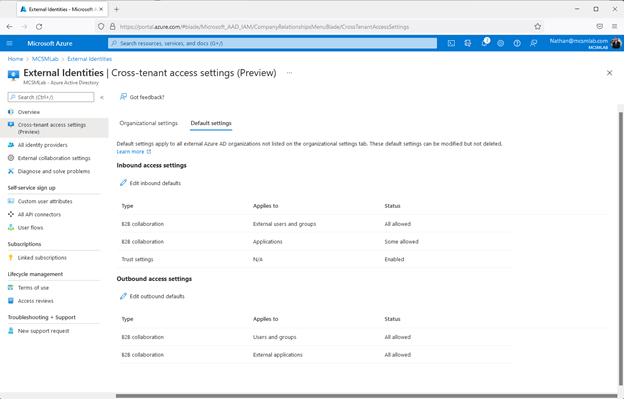
Inside of this portion of the instrument, you can control the cross-tenant accessibility options that utilize to all other Azure Advert tenants. Visitor buyers from other organizations that are not setup with certain options of their possess will obtain their access options from right here.
As proven over, the configurations are divided into inbound and outbound options. The inbound and outbound options are further more separated into B2B collaboration for users and groups and apps. The inbound configurations also have a part for have faith in settings.
The believe in options let you to believe in the MFA set up, compliant gadgets, and Azure Advert joined gadgets from other tenants. I would advocate leaving these options off in this article, not allowing default rely on for exterior businesses safety configurations. If you’d like to belief the MFA, grievance products, or Azure Advert joined device options from yet another group that can be performed exclusively for each and every organization under the “organization settings” part.
Continuing with the inbound options for B2B collaboration. Listed here you can make it possible for or block all external access for end users and groups or by application. “B2B collaboration inbound accessibility configurations lets you collaborate with individuals outdoors of your group by allowing them to signal in employing their possess identites [sic]. These buyers come to be visitors in your Azure Advertisement business.”
The identical settings are obtainable underneath the Outbound accessibility options. The variation is these configurations command the access customers from your Azure Ad tenant will have in other tenants. Of course, you can’t grant your buyers obtain to any other tenant, but these configurations can restrict the accessibility you customers have in other tenants.
The purposes segment makes it possible for you to modify the entry placing by application instead of users or teams. You can add distinct apps to this portion. I additional “Office 365 SharePoint Online” as shown in the screenshot under:
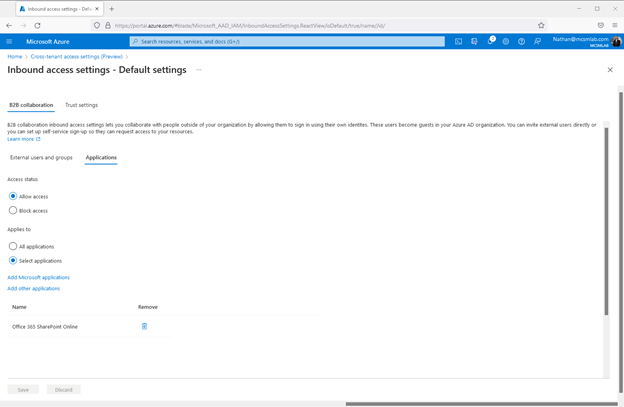
The “Allow accessibility/Block Access” radio button less than “External consumers and groups” and underneath “Applications” have to each be set to both allow for or block. If I check out to set block entry below programs when allow for access is set beneath External end users and groups, I get the following mistake:
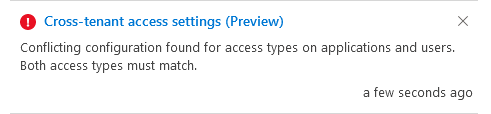
On top of that, the “Applies to” section does not permit you to allow for or block particular apps independently. As the function is at the moment, I do not see any motive to muck with the “All purposes/Decide on applications” radio button as the previously mentioned “Allow entry/Block access” variety will implement to everything. I don’t see a way to enable obtain to SharePoint Online whilst blocking entry to Exchange On the web. I’m likely to suppose that little bit of features will evolve. This attribute is nonetheless in Preview. I hope and count on that will be fixed just before this aspect moves to common availability.
Going on from the default options to the organizational settings, this portion allows you to modify the default settings for unique corporations you incorporate. I would advise leaving the default configurations portion as it is for safety causes and including unique extra permissions to certain corporations right here.
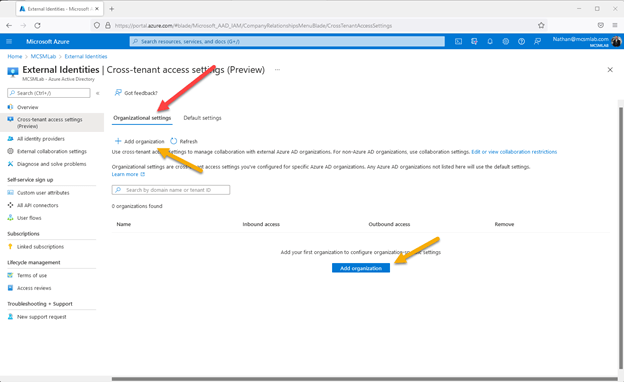
To check this out, I spun up a examination tenant from the Microsoft Developer portal. In the screenshot higher than, the environmentally friendly arrow stage to where by you’ll go to include an exterior group. Each buttons do the very same point, so I’m not guaranteed why Microsoft put the exact same button on this website page two times.
You can add a further firm below making use of both the tenant’s name (mcsmlab.com, or mcsmlab.onmicrosoft.com both equally get the job done for my tenant), or utilizing the Tenant ID. The screenshot down below displays the interface exactly where I additional a exam tenant to my possess tenant.
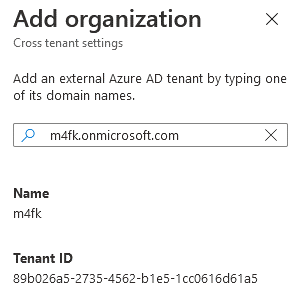
As soon as a tenant is added below, the cross-tenant accessibility settings portal will glance like this:
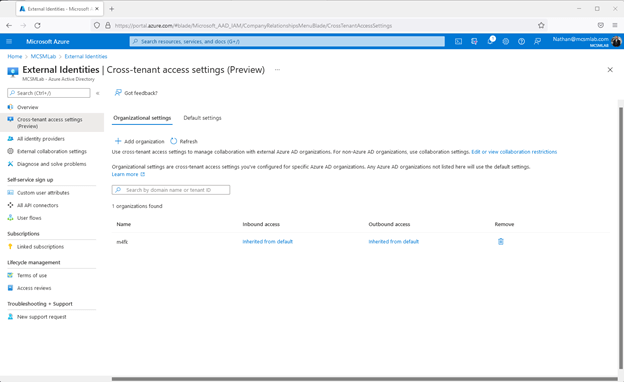
As you can see there, equally inbound and outbound options are at first set to “inherited from default”, which allows the identical entry for customers from and to that business as if you had not added that business below at all. On the other hand, I now can personalize all the setting I talked about earlier mentioned for this certain group. Clicking on the blue “Inherited from default” for either inbound or outbound obtain settings lets me to customize obtain configurations for customers from that certain Azure Advertisement tenant.
So now we’re all performed right? Customers from the m4fk exam tenant should have obtain to all my assets set up in my mcmslab tenant?
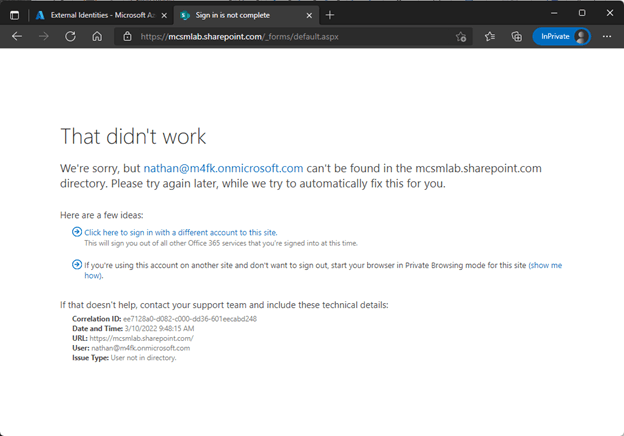
Nope.
These cross-tenant obtain settings do govern the access consumers from the m4fk tenant would have to sources within my mcsmlab tenant but adding an group does not develop guest accounts.
The cross-tenant obtain options permit you to modify the entry that visitor buyers from other companies will have with their visitor accounts. Each person from the other organization will however need to have a visitor account set up in your tenant, and permissions within the distinct apps in your tenant they will be accessing. You can invite exterior end users instantly or you can setup self-service indicator-up so they can request accessibility to your resources. That procedure is unchanged by this new performance.
This tool lets you to promptly limit the obtain that guest end users from other tenants will have in your tenant. It does not grant new cross-tenant functionality, or even make the current cross-tenant functionally do the job “better”. It does not give you an easy way to create a new World-wide Address Record in Exchange On-line that will incorporate buyers from an additional tenant, or routinely grant entry to all your SharePoint Online web pages to end users from an additional tenant with a couple of clicks.
Think of the new element as a way to simply and globally limit collaboration settings in your tenant, not as a way to let people from an additional group to function in your tenant.
Active Directory Checking and Reporting
Lively Listing is the foundation of your network, and the structure that controls obtain to the most vital resources in your business. The ENow Energetic Directory Checking and Reporting software uncovers cracks in your Energetic Listing that can result in a protection breach or poor close-consumer knowledge and allows you to rapidly identify and get rid of end users that have inappropriate access to privileged groups (Schema Admins, Area Administrators). Even though ENow is not an auditing software program, our experiences reduce the quantity of operate necessary to deal with HIPAA, SOX, and other compliance audits.
Accessibility your No cost 14-day demo to accelerate your safety awareness and simplify your compliance audits. Features full library of reviews.




